In today's hyper-connected world, critical infrastructure organizations are at the forefront of the digital revolution. From power grids to transportation systems, these sectors play a pivotal role in ensuring the functioning of society. However, with increased connectivity comes heightened cybersecurity risks, making it imperative for critical infrastructure organizations to achieve cybersecurity maturity.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a robust and flexible framework to enhance an organization's cybersecurity posture. In this blog, we will explore how critical infrastructure organizations can achieve cybersecurity maturity by embracing the NIST Framework.
Understanding the NIST Cybersecurity Framework
The NIST Cybersecurity Framework was created to help organizations identify, assess, and manage cybersecurity risks. It offers a structured approach that aligns with best practices and industry standards, empowering organizations to strengthen their cybersecurity defenses.
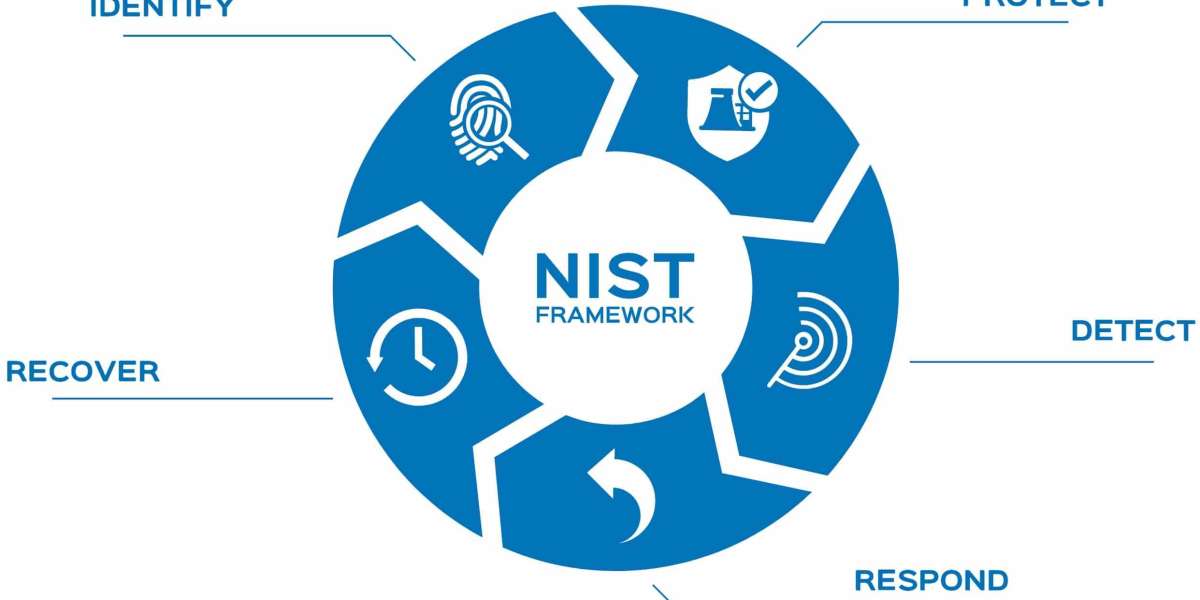
The NIST Framework comprises five core functions: Identify, Protect, Detect, Respond, and Recover. Each function represents a critical aspect of cybersecurity management, enabling organizations to tailor their strategies to their unique needs and risks.
- Identify: Know Your Assets and Risks
The first step in achieving cybersecurity maturity is to identify and understand the organization's critical assets, data, and systems. Critical infrastructure organizations must conduct a thorough assessment of their infrastructure, evaluating potential vulnerabilities and threats. By understanding the risk landscape, they can prioritize efforts and allocate resources effectively.
- Protect: Implement Strong Security Measures
The Protect function emphasizes the implementation of safeguards to protect critical assets from cyber threats. This involves implementing access controls, encryption, multi-factor authentication, and robust security policies. Regular employee training and awareness programs also play a crucial role in building a security-conscious culture.
- Detect: Early Threat Detection
Detecting threats early is essential to mitigate potential damage. Critical infrastructure organizations must deploy advanced monitoring and intrusion detection systems to identify suspicious activities promptly. Continuous monitoring helps in detecting and responding to cyber incidents before they escalate.
- Respond: Swift and Effective Response
No organization is entirely immune to cyber incidents. The Respond function emphasizes developing an incident response plan that outlines clear roles and responsibilities during a security breach. This proactive approach allows organizations to contain and neutralize threats swiftly, minimizing the impact of an incident.
- Recover: Bounce Back Stronger
The Recover function focuses on restoring normal operations after a cybersecurity incident. Having a well-defined recovery plan ensures that critical infrastructure organizations can recover quickly and efficiently, minimizing downtime and disruption to essential services.
Embracing Cybersecurity Maturity
Achieving cybersecurity maturity is an ongoing journey for critical infrastructure organizations. It requires a proactive and dynamic approach to cybersecurity management. Here are some essential strategies to enhance cybersecurity maturity:
- Collaboration and Information Sharing: Critical infrastructure organizations should collaborate with industry peers and share threat intelligence. This collective effort can strengthen the overall cybersecurity posture and foster resilience across the sector.
- Regular Assessments and Updates: Regularly assess the effectiveness of security measures and update cybersecurity strategies to adapt to evolving threats. Embrace a continuous improvement mindset to stay ahead of cyber adversaries.
- Leadership Commitment: A strong commitment from senior leadership is vital to drive a culture of cybersecurity throughout the organization. Leaders should prioritize cybersecurity investments and support ongoing training initiatives.
- Third-Party Risk Management: Critical infrastructure organizations often work with third-party vendors. Implementing a robust third-party risk management program ensures that cybersecurity standards are upheld throughout the supply chain.
Conclusion
Cybersecurity maturity is not an endpoint; it is a journey that requires dedication, collaboration, and continuous improvement. For critical infrastructure organizations, embracing the NIST Cybersecurity Framework provides a solid foundation to build a resilient and secure digital infrastructure. By identifying risks, implementing strong security measures, and fostering a proactive cybersecurity culture, these organizations can protect essential services and play a crucial role in securing the digital future of our interconnected world.